Embedded systems have long been dominated by C and C++, but Rust has emerged as a superior language that addresses the inherent shortcomings of these established languages while offering modern features designed for safety-critical and performance-sensitive applications
Schedule migration demoRust shifts developers' focus from managing memory to resource ownership. While C/C++ developers manually handle pointers and memory references, Rust enforces ownership, ensuring memory safety at compile time.
If the code has ambiguous ownership or unclear variable lifetimes, the compiler will refuse to compile it, catching issues before they turn into runtime bugs.

%20(2).png)
Ensuring memory safety without sacrificing performance is essential in embedded systems. C and C++ offer manual memory management but introduce common vulnerabilities like buffer overflows and use-after-free errors. While garbage-collected languages avoid these issues, they add runtime overhead and unpredictable pauses.
Rust solves this dilemma by eliminating memory vulnerabilities at compile time through its ownership system and borrow checker, without requiring a garbage collector that would compromise performance in critical control systems.
Rust enables developers to write high-level, expressive code while maintaining performance. Unlike C++, where abstractions can incur hidden runtime costs, Rust’s zero-cost abstractions ensure that higher-level constructs are compiled into efficient, low-level machine code with minimal overhead.
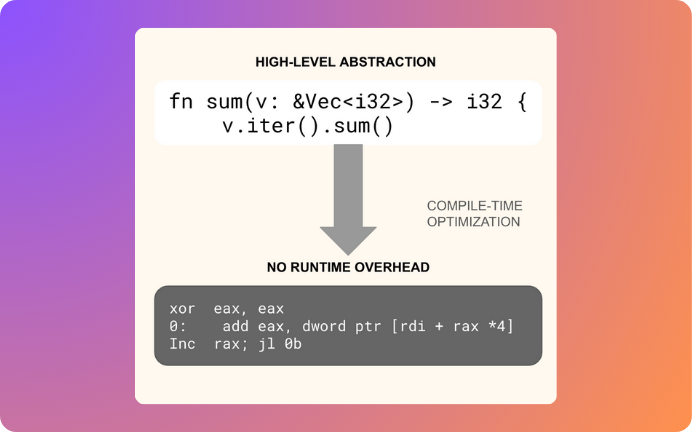

Rust’s powerful type system eliminates entire classes of common errors at compile time. Features like algebraic data types (`enum`s) and exhaustive pattern matching enable developers to write more expressive and error-resistant code compared to C and C++.
Hackers exploit common attack vectors in embedded systems, targeting memory vulnerabilities, insecure protocols, and weak authentication. Rust’s safety features help mitigate these threats.
Buffer overflows are a common attack vector in C and C++. Attackers exploit unchecked memory writes to overwrite adjacent memory, often inserting malicious code. Rust's memory safety model prevents buffer overflows at compile time.
These occur when memory is accessed after it has been deallocated, leading to the potential execution of arbitrary code. Rust’s ownership model ensures that references cannot outlive their allocated memory, eliminating this vulnerability.
Exploited in concurrent applications where multiple threads access shared memory unsafely. Rust enforces strict thread safety guarantees, preventing data races at compile time.
Attackers manipulate memory allocations to gain control over a system. Rust’s structured memory safety mechanisms mitigate these issues by preventing unintentional stack and heap corruption.
Many embedded systems communicate over networks, making them vulnerable to attacks like Man-in-the-Middle (MitM) and replay attacks. Rust’s cryptographic libraries and secure coding practices help developers implement robust encryption and authentication mechanisms.
Attackers often attempt to inject malicious code by exploiting memory corruption vulnerabilities. Rust’s strict compile-time checks and memory safety guarantees make it extremely difficult for an attacker to execute unauthorized code.
Rust’s tooling ecosystem, including `cargo` (its package manager and build system), `clippy` (linter), and `rustfmt` (formatter), provides a streamlined development experience. The Rust compiler offers extremely detailed and helpful error messages, reducing debugging time and improving code quality.


Interacting with hardware requires precise control over memory and peripheral registers. While C and C++ provide this flexibility, they also expose developers to risks of undefined behavior. Rust’s `unsafe` keyword allows low-level control where necessary, but it forces developers to explicitly mark and justify unsafe operations, encouraging safer patterns.
Several forward-thinking organizations are already working on Rust for safety-critical domains.

C++ embedded systems rely on optional safety measures that require substantial developer discipline, specialized tools, and manual verification. Rust's approach is fundamentally different, with built-in guarantees enforced by the compiler—ensuring memory safety, concurrency protection, and type safety without runtime overhead.
Experience the future of control software